
Von Ryan Petroschka Consulting zu uwuWARE
1. April 2025
Ein neuer Name. Eine klare Mission. Noch mehr digitale Power.
Was als persönliche Beratung begann, hat sich zu einem starken Partner für IT, Software und Cybersecurity entwickelt. Aus diesem Grund haben wir uns entschieden, einen neuen Schritt zu gehen – Ryan Petroschka Consulting wird zu uwuWARE.

IT Security Kill Chain
1. März 2025
Attacks on IT systems are a constant threat to all organizations. The IT Security Kill Chain model has been developed by Lockheed Martin to allow organizations to gain a better understanding of the stages of an attack and develop strategies to stop attackers early in the process.

Password Best-Practices
1. November 2024
Passwords are the first line of defense against IT threats. They protect our personal and professional information from unauthorized access. However, despite their critical role, many people still struggle with password management.

The Basics of Encryption
1. August 2024
In today’s world, sensitive information is being transmitted and stored online more than ever before. This sensitive information can include personal data, financial information, and confidential business data.
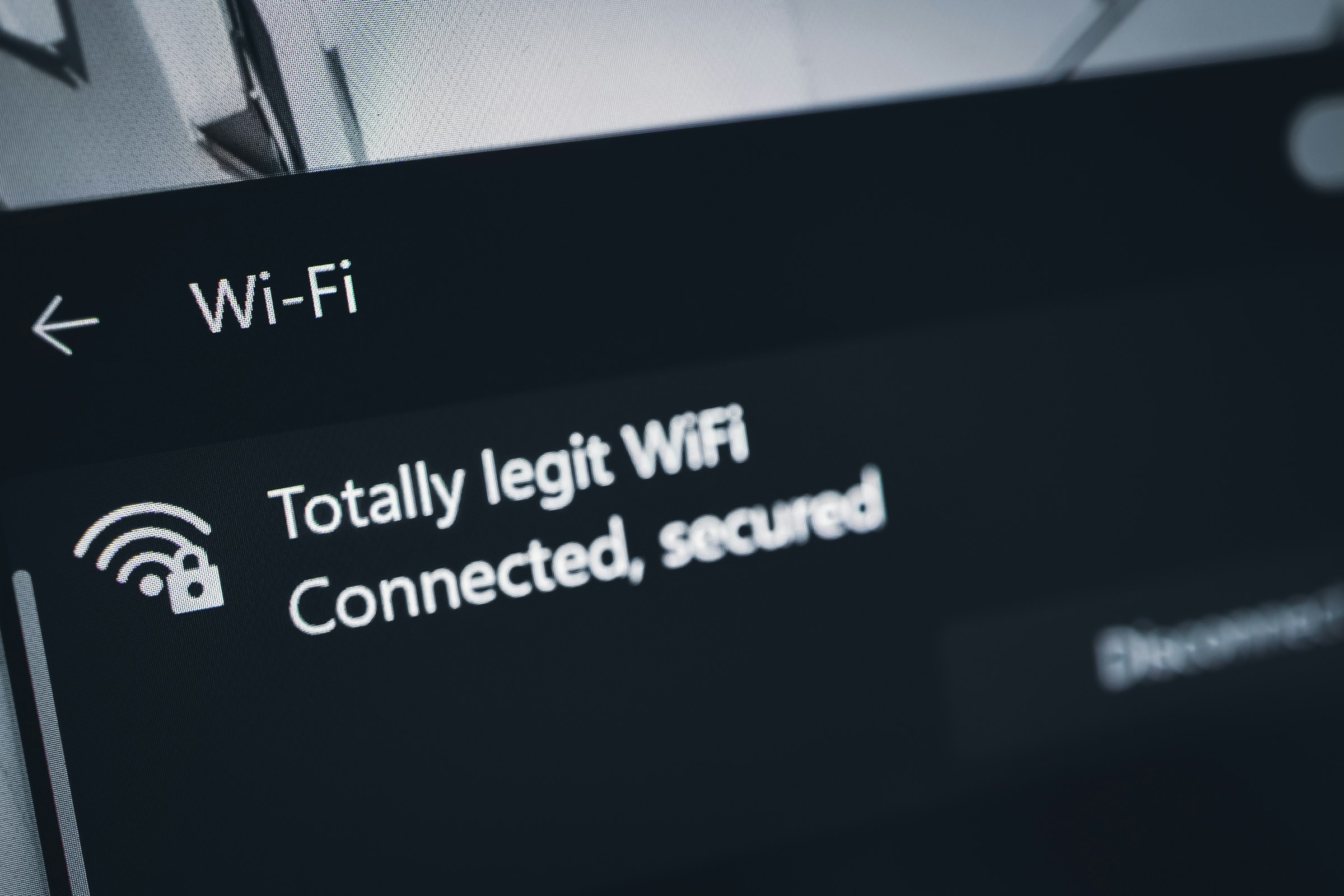
IT Security Awareness for Employees
1. Mai 2024
IT security is a dynamic field, and as new risks arise, businesses will need to keep their employees informed. IT security training should be done at the very least once a year, but even that infrequently can put firms at risk.

Environmental Footprint of Datacenters
1. April 2024
Data centers consume a significant amount of energy, accounting for roughly 1.8 % of total electricity consumption in the United States. Data centers are responsible for about 0.5 % of total US greenhouse gas emissions.
Neueste Artikel

Zero-Trust Security: A Proactive Approach to IT Security
1. Dezember 2024
The traditional approach to IT security, known as “trust but verify,” assumes that users and devices inside the network are trustworthy, while those outside the network are not. However, this approach has proven to be inadequate in the face of increasingly sophisticated attacks.

Password Best-Practices
1. November 2024
Passwords are the first line of defense against IT threats. They protect our personal and professional information from unauthorized access. However, despite their critical role, many people still struggle with password management.

Social Engineering: An inside threat
1. Oktober 2024
Social engineering is a type of attack that relies on human interaction to gain access to sensitive information or systems. Unlike other types of attacks, social engineering attacks don’t rely on technology or hacking skills. Instead, they rely on psychological manipulation to trick individuals into revealing confidential information or making them perform actions that compromise their security.

Two-Factor Authentication: An Essential Layer of Security
1. September 2024
Two-factor authentication (2FA) is a security process that adds an extra layer of protection to your online accounts. It requires you to provide two pieces of information in order to access your account – something you know (such as a password) and something you have (such as a smartphone).

The Basics of Encryption
1. August 2024
In today’s world, sensitive information is being transmitted and stored online more than ever before. This sensitive information can include personal data, financial information, and confidential business data.

Bring Your Own Device Security
1. Juli 2024
“Bring Your Own Device” continues to be a huge opportunity as well as a major challenge for businesses. Learn how to harvest the benefits of allowing employees to work on their own hardware and minimize IT security risk by taking the proper approach to develop effective BYOD policies